Lesson 1
Introduction to Enterprise Identity and Access Control
In this introductory lesson, we meet the course instructor and discuss enterprise identity and access control from a high-level perspective.

Course
This course focuses on identity and access management. As a security architect, implementing an organization-wide strategy for strong Identity and access management can greatly improve the security posture of the organization. IAM can be tricky to architect and implement. Too much access can lead to data exposure, whereas, too little access can lead to business hindrance. A fine balance is required while designing a strong IAM model. We will be covering some of those concepts and methodologies in this course.
This course focuses on identity and access management. As a security architect, implementing an organization-wide strategy for strong Identity and access management can greatly improve the security posture of the organization. IAM can be tricky to architect and implement. Too much access can lead to data exposure, whereas, too little access can lead to business hindrance. A fine balance is required while designing a strong IAM model. We will be covering some of those concepts and methodologies in this course.
Intermediate
4 weeks
Real-world Projects
Completion Certificate
Last Updated May 5, 2023
Lesson 1
In this introductory lesson, we meet the course instructor and discuss enterprise identity and access control from a high-level perspective.
Lesson 2
In this lesson, we discuss two access control methodologies in detail, RBAC and ABAC. We also create IAM Roles and review IAM policies in AWS.
Lesson 3
In this lesson, we discuss mapping permissions using an access control matrix design based on access control requirements.
Lesson 4
In this lesson, we take a deep dive into evaluating IAM policies, creating IAM restrictions, and validating permissions in AWS.
Lesson 5
In this lesson, we focus on building an IAM architecture diagram that visualizes and defines the organizational structure of users, permissions, and resources.
Lesson 6
In this lesson, we wrap up the course by focusing on monitoring policy compliance, enforcing IAM policy configurations, and policy remediation in AWS.
Lesson 7 • Project
In this project, you will implement and enforce identity access management within AWS by implementing a role structure with policies that will be evaluated and enforced.

Senior DevOps Engineer
Sjon-Paul Brown is a DevOps Engineer and DevOps Consultant who helps companies streamline and secure their cloud environments and development processes. He has formally worked with varying startups and enterprises to ensure to that software can be securely developed and deployed in an agile manner.
Combine technology training for employees with industry experts, mentors, and projects, for critical thinking that pushes innovation. Our proven upskilling system goes after success—relentlessly.

Demonstrate proficiency with practical projects
Projects are based on real-world scenarios and challenges, allowing you to apply the skills you learn to practical situations, while giving you real hands-on experience.
Gain proven experience
Retain knowledge longer
Apply new skills immediately
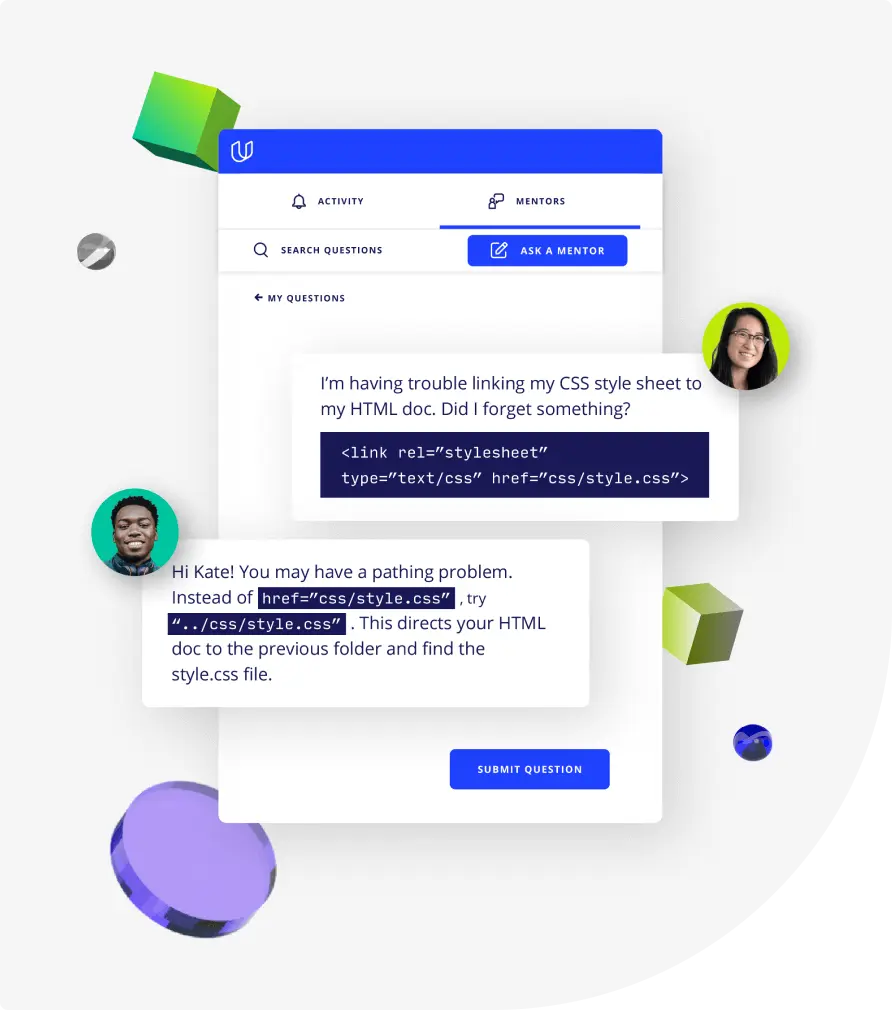
Top-tier services to ensure learner success
Reviewers provide timely and constructive feedback on your project submissions, highlighting areas of improvement and offering practical tips to enhance your work.
Get help from subject matter experts
Learn industry best practices
Gain valuable insights and improve your skills
Unlimited access to our top-rated courses
Real-world projects
Personalized project reviews
Program certificates
Proven career outcomes
Full Catalog Access
One subscription opens up this course and our entire catalog of projects and skills.
Average time to complete a Nanodegree program
4 weeks
, Advanced
4 weeks
, Beginner
4 weeks
, Beginner
1 week
, Advanced
4 weeks
, Intermediate
4 weeks
, Beginner
3 weeks
, Advanced
4 weeks
, Intermediate
4 weeks
, Intermediate
4 weeks
, Beginner
(416)
4 months
, Intermediate
(174)
2 months
, Advanced
8 hours
, Beginner
4 weeks
, Intermediate
(9)
4 months
, Intermediate
4 weeks
, Intermediate

Enterprise Identity and Access Control
4 weeks
, Advanced
4 weeks
, Beginner
4 weeks
, Beginner
1 week
, Advanced
4 weeks
, Intermediate
4 weeks
, Beginner
3 weeks
, Advanced
4 weeks
, Intermediate
4 weeks
, Intermediate
4 weeks
, Beginner
(416)
4 months
, Intermediate
(174)
2 months
, Advanced
8 hours
, Beginner
4 weeks
, Intermediate
(9)
4 months
, Intermediate
4 weeks
, Intermediate